A Unique Look at Securing Remote Users in 2021
Hi Everyone,
This week I am showcasing a colleague of mine.
Thomas Llewellyn shares his thoughts on remote security!
Roughly a year ago COVID-19 was declared a pandemic by the WHO and a mass exodus of employees from their office workplaces, into their homes, was commenced. This brought with it a number of urgent technical challenges which fell upon the shoulders of IT personnel worldwide, and are still being dealt with today.
The sudden need to support and secure an entire company's staff while they worked remotely was an issue that many organizations were not prepared for; administrators and supporting IT personnel had to think quickly to come up with a solution that was viable, and could be implemented as painlessly as possible.
Today I would like to look at what happened over the last year, as well as some of the major security issues that come with supporting remote users. Finally, I will shed light on how a small cybersecurity firm from California has come up with a simple solution works so well its a mystery that not more people are doing it.
The Great WFH Migration of 2020
At the time, the move to a WFH (Work From Home) model forced organizations to to quickly come up with ways to enable their employees to stay productive while keeping business assets safe, and IT departments or MSPs were tasked with implementing these solutions.
No problem, right? The tasks related to supporting remote users is part of the bread-and-butter of being an everyday IT hero:
• Setting up remote access to desktops
• Installing VPN clients for secure access to company networks and assets
• Imaging company-issued hardware and creating Domain logins for Group Policy controls
This time it was different though: the sheer volume of users that suddenly needed to be supported, coupled with the growing trend of moving to cloud-based solutions, opened what I can only imagine was a Pandora's box of problems for IT staff around the globe.
So how did companies handle this? Speaking to different people about how their organization handled the sudden move to working from home, (and having experienced it first hand while attending classes at SAIT), I have heard an entire range of responses: from horror stories to it being "just another day" at the office.
Business As Usual
Some businesses, especially (modern) software development firms, already hosted their resources on cloud-based repositories like GitHub, and working from home just meant more time for coffee in the morning 🌞☕ 👍. Many of these businesses also communicated over collaboration apps like Slack, and video conferencing apps like MS Teams comes with Microsoft 365 Enterprise subscription, which many of them had.
All that was left was to do was implement new company policies on making pants a requirement for the morning scrum meetings...
Virtualization? Cloud? What's That?
On the other end, some company's lack of investment into their information infrastructure left them with little-or-no choice on how to get everyone working from home
(Trigger Warning! If you are currently working in IT, the following story may cause you some distress.)
A (very) large energy company in Alberta sent all their employees home with their personal desktops.
I don't think I need to go into too much detail with you about what kind of nightmare that would be to manage, (any more than it must have ALREADY been), but a few things do come to my mind:
• IT and its abilities to protect and support a business did not seem to be a priority in that company.
• Now that everyone took their desktops home, how are these being managed and kept safe?
o Backups?
o VPN?
o Remote desk... oh, right, nevermind 🙄
And let's think of the users for a moment:
• Where are they supposed to plug in this computer?
• Are they now covering the added energy cost of running a desktop in their home?
• What about the additional risks that come with working from home? Having a company desktop left unlocked while other small (and curious!) family members are around, is a definite added security risk.
When I hear stories like this, I can only think of how many times the IT team approached upper management, begging for them to approve a move to something more manageable (virtualization, cloud-based infrastructure, etc.), only to have it deemed an unnecessary expense.
IT is often viewed as nothing more than an unwarranted cost, and unfortunately, the brunt of work that arises in these kinds of disasters falls on the very people who tried to prevent it in the first place. My heart goes out to you.
So the response to the pandemic and WFH runs the entire gamut of excellent to awful, which seems to have been directly related to how well that business managed their information infrastructure.
Now lets take a closer look closer at some of the specific security concerns that were being addressed, and why they may not provide an adequate solution for the issues at hand.
Security Concerns When Working From Home
The traditional "castle model" of workplace cybersecurity was suddenly made obsolete with the shift to working from home. This model had been slowly diminishing for some time, and now some major changes needed to be made, ASAP. If an organization hadn't already implemented a Zero-Trust network approach, they certainly needed to do it now: Every employee was connecting from a network outside of the company, on an undetermined number of devices of varying types.
How can these devices and their connections to the company network be secured? Sure, if it's a handful of employees, just image a couple laptops, give them Domain logins, and a VPN client to connect to the network. Next step, run sfc/ SCANNOW on a troubled user's computer, and go for coffee, right??
Okay but what if it's every employee? Does your organization even have that many take-home devices?
How quickly can VPNs clients be set up on every device? And, let's be honest: does a VPN really secure an end device that will be on the same network as other family members who might be answering calls from "Microsoft Support"? ISPs will need to be contacted, as a major uptick in bandwidth is about to be seen, and the servers handling those incoming connections better be beefy enough handle it all.
On top of that, with the growing popularity of cloud-based solutions like SaaS, what if the users don't even need a dedicated tunnel to the company network? All they need is a browser, and they can go about their usual business. Hey, no worries then, right?! Wrong! Have you seen the number of toolbar addons that some people have installed on their personal computers? A VPN wouldn't save this device from malicious activity; for all you know, its already compromised, and probably needs the IT equivalent of an exorcism...
Alright, working remotely brings with it some serious security (and logistical) concerns, and traditional approaches of VPNs and company-issued devices aren't going to adequately cover them. Both end-users and IT admins need a good solution to keep everyone working safely: What's the best answer here?
From my (limited) perspective, the solution needs to include at least these basic four (4) points:
1. Users need to have some kind of hardware that can perform their normal work-duties
• If they already own a desktop that can do their work, why change that?
• If they need a laptop or other company-issued device, then so be it (but please, don't send them home with a Desktop!)
2. Any connection to the company network needs to be secure, originating from a Zero-Trust network of it's own
• I'll get to this, but as we already discussed: a VPN does not prevent the spread of the latest ransomware, caused by a teenager's visit to a shady website. Much less: it now has a dedicated tunnel to your servers. Yay!
• Zero-Trust needs to start at home! ("I'll take: 'Worst-sounding true statement of 2021' for $800, please" ✋)
3. It needs to be as simple as possible for end users
• Or else they will simply find an easier (and less secure) way of doing it.
• Imagined Support Phone Call with Bill from Management (sorry to any Bills out there reading this): "Okay Bill, now log in to the new Router that we sent home with you, and just partition the network into VLANs..."💀
4. Lastly, the solution needs to fall within a reasonable cost for the company.
• Buying 100s of new laptops and setting them up for remote work may be doable by an elite unit of IT technicians, but is there a more cost-effective (and faster) way of doing this?
There are probably more considerations, but what if I told you that all of these points could be achieved with a single device, that takes less than 5 minutes to set up, with ZERO configuration for the end user?
Cyberlucent's SecureWorkHome (SWH) Device
I recently had the pleasure of meeting with the team from Cyberlucent, a cybersecurity firm based in California, with offices here in Calgary and Ottawa. They have come up with a unique approach to solving the problem of working securely from any location, and it's so simple it's almost unbelievable:
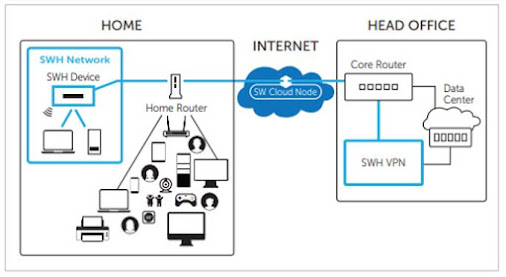
Piggybacking on the hardware of the Unity Dream Machine, Cyberlucent has made the SWH Device: a "Fully segmented, firewall protected, zero-trust, network segment operating within an otherwise unsecure network environment." All a user needs to do in order to get up-and-running is plug the SWH device into their router, and then connect their own device to it. On the other (business) end, the SWH device can connect from it's cloud node to an existing VPN server, or a dedicated SWH server. (See the images below, illustrating the different setup options).
As an added benefit, the network is continuously monitored by Cyberlucent's proprietary security AI, Cytheia, which "applies advanced data analytics, artificial intelligence, and machine learning to “see” into network traffic streams and […] extract[s] actionable cyber risk information". Come at me, hackers.
Uh, What?
After our conversation, I went straight to Google: Surely, the market would be flooded with these kinds of solutions. It's too simple; others must have thought of this already, and have market-ready solutions for me to choose from.
It turns out: it's not. There are some solutions out there, but having it all packaged together in one simple plug-n-play device has not become widely available yet.
Why aren't more companies doing this? I don't have an answer, but rather, I would like to open it to you:
• What do you think of third-party solutions like this?
• What are the serious drawbacks you see?
• Are there other obvious solutions to working from home that you wish industry professionals knew about?
Maybe more companies offering these types of solutions will start popping up, but with the exponential rise of security threats, and the birth of things like Malware as a Service, I only hope that organizations act quickly and prudently to implement them