[1]
The other day I did an experiment. I wanted to see what would happen if I attached a bridged VM to a public network and have an FTP server running.
I only had port 21 open on the firewall and the FTP server was read only (anonymous/anonymous).
I wanted to see how long it would take for someone to connect to my FTP server.
It took no time at all and I had people downloading my garbage text files. ( I am going to be writing another article about my findings and lessons learned through this activity)
However this article is not about people's inherit drive towards voyeurism. It's about how I optimized my use of Wireshark to watch the traffic interacting with the server.
Capture Filters VS. Display Filters:
These two terms (Capture/Display) often get mixed up. The filter that is predominantly used is display filter.
When a new user starts using Wireshark they open it up and select "Start Capture". Immediately they see all the packets being captured on the network. As the packets are being captured live, the user can type in the text box at the top various commands that will be used to filter incoming packets as they are captured.
This is extremely useful as you can literally watch for anything. If the "stuff" you want to watch for can exist in a packet then you can filter on it. The display filters can be incredibly specific and complicated, especially when (and you will) incorporate operators (or,and,eq,ne, etc).
Display filters can filter live traffic which as I have said is very handy. In addition to this you can save and export captures and conduct the same filtering on the .pcap file.
So what is a Capture filter?
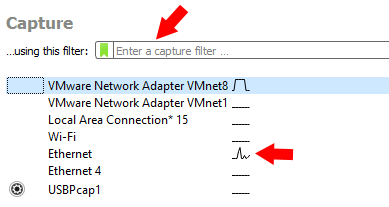
Take a look at this picture above, when you first open Wireshark you have an option to choose a Capture. Essentially how this type of filter and capture works is that before you start sniffing on the network you tell Wireshark exactly what it is you want to capture, everything else is ignored.
For example:
I want to capture traffic that is coming to and from a particular host on the network
My capture would look like this host <IP>
The captures don't stop here, see below the listed options you can use to specify the capture filter.
host
port
net
portrange
ether
tcp
ip
ip
arp
gateway
broadcast (does not include unicast traffic)
less (less than, followed by a length)
greater (greater than, followed by a length)
Operator
and(&&)
or(pipe pipe)
not(!)
So the primary difference between display and capture filters is that capture grabs only specific requirements (with it's own set of unique commands) and display filter sorts through ALL the packets as they are captured or through a saved file.
If you are wondering can you do both. YES! One could do a capture filter and then export the content and then use display filters to dig deeper.
Why did I choose Capture Filter?
I chose it because I wanted to have a small file to export at the end, and I did not want to filter through "junk" that I knew I would not need.
Using capture filters allows for efficient network monitoring and can actually be used during a pentest engagement.
During an engagement your client may accuse you of impacting assets that you actually did not have any interaction with. When you are conducting your scans if you have a capture filter running monitoring your ether you can use this capture as evidence to prove that your actions had nothing to do with the supposed failure with the client asset(s).
Thanks for reading!
Here is a video reference of what was discussed here
Reference:
[1]picture:https://infosecwriteups.com/getting-started-with-wireshark-part-1-begginers-tutorial-for-wireshark-protocol-analysis-using-682f1535e2fe