Detecting Brute Force Attack - Wireshark
There are a variety of network attacks that are visible over the network. From DOS, MiTM, Network Scans, Spoofing and then to what we are discussing today, Brute Force Attacks.
Brute Froce(BF) can also be referred to as a dictionary attack. How a BF attack works is that a piece of software, perhaps hydra, cycles through a wordlist containing thousands of potential user/passwords. For each attempt to login a connection is established and authentication is attempted. If the authentication fails then the software will keep going till it finds the correct combination.
BF attacks are noisy and create a lot of network traffic. As far as network attacks go they are the equivalent of bashing a baseball bat against a door until the door gives way. If that were happening at your house, you would likely notice.
These are my steps to discovering BF attack in your network.
1. "Drive-By"
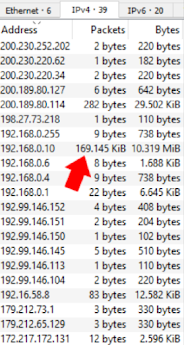
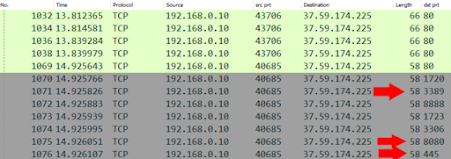
I always start here. I have never heard anyone else do it. But it is so useful because there are patterns of colours that give us a clue as to what is happening. Picture 1 is of the scroll bar. Picture two is of SYN and RST packets which is a clear sign of a scan occurring. We know a scan is occurring because SYN packets are being sent to the same destination machine, the destination port is changing and the source port is staying the same.
2. Identify Attacker
Without even applying any filters we have also identified our target. Looking at the scan traffic we can see that 192.168.0.10 is conducting a port scan of machine 37.59.174.225
3. Isolate Communication
My capture has a total of 174,985 packets. That is a lot.
I only want to see traffic from attacker > target
so I apply this filter
ip.src==192.168.0.10 and ip.dst==37.59.174.225
This shrinks the list windows down to 52% displayed. We have cropped out 48% of traffic we don't need to look at. Awesome!
4. Observe Behaviour
Of these packets the first 10 are ICMP requests. Basically the attacker saying "Hey you there?" After this the attacker starts bumping around on the web server that is hosted. Nothing really weird about the web traffic. At packet 1010 the scan begins.