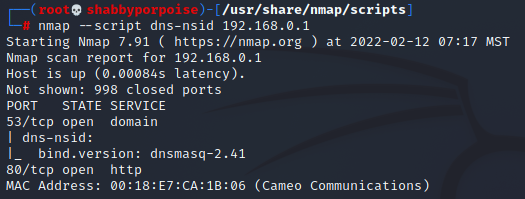
Essentially this is a banner grab for a DNS server. Infomation gathered is the DNS' nsid or "Name Server ID".
The retrieved information will show server ID and bind version.
The purpose of discovering DNS banners is to determine if the DNS sever has BIND vulnerabilities which can explose DNS servers to remote attacks.
Same results but this time we specify a port
Changing the scan slightly. We are sending UDP packets at the target on a specific port. Notice that between this final scan and the previous scans we have determined that that the DNS port is responsive to both TCP and UDP packets.
Whenever you see the DNS port state open with TCP as it's protocol you should dig in and do some exploring. There is an increased probability that there is a vulnerability present.
Reference: [1]https://nmap.org/nsedoc/scripts/dns-nsid.html